Updating MySQL Pre-4.1 Password Hashes to be MySQL 5.6 Compatible
Skip to end of metadataGo to start of metadata
With the release of MySQL 4.1, the password hashing mechanism was updated to produce more secure passwords. MySQL continued to support the old MySQL password hashes for compatibility reasons until MySQL 5.6. When upgrading to MySQL version 5.6 (or the MariaDB equivalent) or higher, MySQL will randomize any passwords using an old password hash. Randomizing the password for MySQL users can prevent websites from connecting to databases properly, and effectively bring the site down.
Password Hashing
Passwords stored in a database (if done responsibly) are not stored in a human readable form. In the event of a security breach, this prevents attackers from having plaintext passwords that can be used to easily access user accounts. Converting passwords to a non-human readable form is where hashing comes in.
Hashing is a process by which a string of characters (a password in this case) is mathematically transformed into a cryptographically secure hash . A hash would look like a series of meaningless random characters, and is stored in a database as a representation of a password. This differs from something like encryption in that hashing isn’t intended to be reversed. A password can be easily converted into a hash, but a hash can’t be easily converted back into a password. When a user tries to authenticate with a password, the password provided then undergoes the same hashing operation, and is compared to the hash in the database. If the hashes match, the user is authenticated, and logged in.
While hashes aren’t supposed to be reversible, it isn’t really true. Hashes can be “cracked”, and converted back to a usable password given enough time, or ingenuity. Hashing functions have evolved, and become more secure as existing hashing functions have been cracked. The hash used by MySQL for passwords prior to MySQL 4.1 is now considered to be a weak hash, and can be more easily cracked in the hands of an attacker. The password hash introduced in MySQL 4.1 is a much stronger hash, and much more difficult to crack.
Locating A Password
If a site connects to a MySQL database, it has to store the name of that database and the user and password used to connect to it somewhere. Usually it’s stored in a flat file, and typically it will be a configuration file.
WordPress
For WordPress, the MySQL user and password is in the wp-config.php file. In that file, look for the definitions of the DB_USER and DB_PASSWORD variables.
define( 'DB_USER' , 'user' ); define( 'DB_PASSWORD' , 'password' );
Joomla
For Joomla, the MySQL user and password is in the configuration.php file. In that file, look for declarations of the $user and $password variables.
public $user = 'user' ; public $password = 'password' ;
If you’re using a version of Joomla prior to 3.0, the location of the MySQL user and password may vary.
Drupal
For Drupal, the MySQL user and password is in the sites/default/settings.php file. In that file, look for the declaration of the $databases array.
$databases[ 'default' ][ 'default' ] = array ( 'database' => 'databasename' , 'username' => 'user' , 'password' => 'password' , 'host' => 'localhost' , 'port' => '3306' , 'driver' => 'mysql' , 'prefix' => '' , 'collation' => 'utf8mb4_general_ci' , );
With older versions of Drupal, the database information may be in a different form.
Magento
For Magento, the MySQL user and password is in the app/etc/local.xml file. In that file, look for the <username> and <password> fields.
<connection> <host><![CDATA[localhost]]></host> <username><![CDATA[user]]></username> <password><![CDATA[password]]></password> <dbname><![CDATA[databasename]]></dbname> <initStatements><![CDATA[SET NAMES utf8]]></initStatements> <model><![CDATA[mysql4]]></model> <type><![CDATA[pdo_mysql]]></type> <pdoType><![CDATA[]]></pdoType> <active> 1 </active> </connection>
Updating Password Hashes
Password hashes will be updated when a user’s password is changed. Changing the password to the same password will simply update the hash without changing anything else. There are a couple methods you can use to change the password.
cPanel
You can quickly update the password for a MySQL user within cPanel.
Go to Databases > MySQL® Databases .
Click Change Password for user you wish to change.
On the following page, you will be able to update the password for the MySQL user.
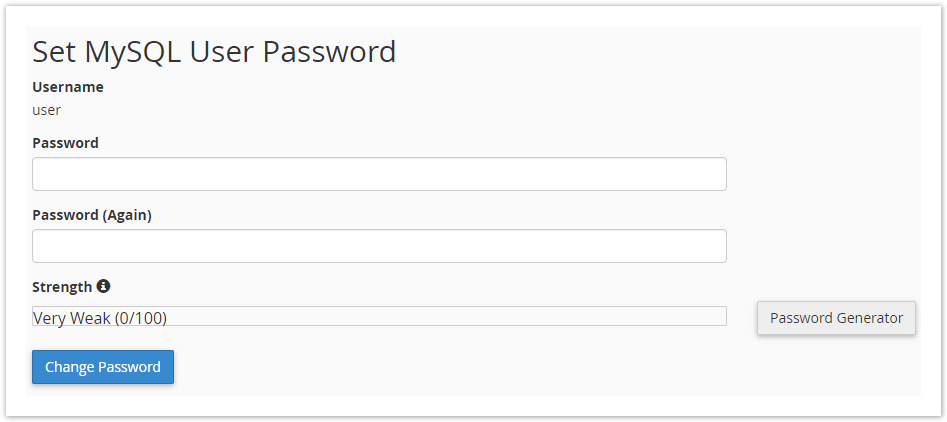
Use the existing password for your website to avoid anything breaking because of the password changing.
If your existing password doesn’t meet the strength requirements set on the server, you can use the Password Generator to randomly generate a strong password. Be sure to change the password in your site’s configuration files if you do change the password.

Finally, click Change Password to save the new password, and update the password hash.
cPanel User
If the MySQL user you need to update is the default user for your cPanel account (the MySQL user will be the same as your cPanel username), you can update the password hash by updating your cPanel password.
Go to Preferences > Password & Security .
On the following page you will be able to update the password for your cPanel account.
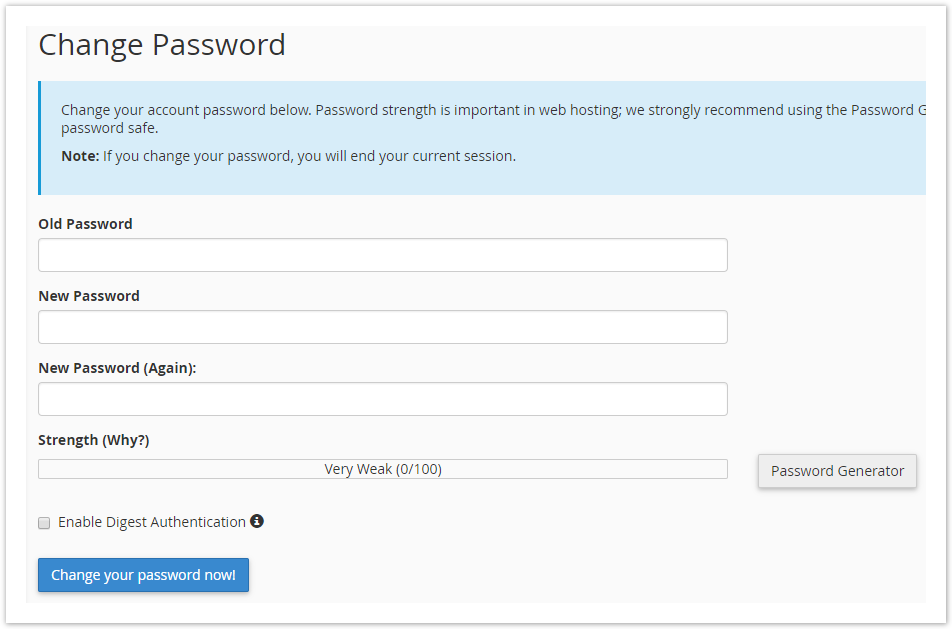
If your existing password doesn’t meet the strength requirements set on the server, you can use the Password Generator to randomly generate a strong password.

Finally, click Change your password now! to save the new password, and update the password hash.

MySQL
The password for a MySQL user can also be changed using a MySQL query. You must run this query as root or another privileged user.
UPDATE mysql. user SET Password = PASSWORD ( 'password' ) WHERE user = 'user' ;
Need Further Assistance?
Please don’t hesitate our 24/7 Technical Support team if you have any questions or need assistance updating a MySQL user’s password hash.
Curated by Liquid Layer Networks
At Liquid Layer Web Hosting [LiquidLayer.net], we’ve made a shared web hosting platform that’s both feature-rich and easy to make use of. Our programmers have built up a custom Linux cloud web hosting platform plus an innovative Control Panel that perfectly takes advantage of its capabilities. After long hours of programming and bug fixing on our end, we are now capable to guarantee that all of our shared web hosting services are safe, virus-free, full of capabilities and very easy-to-work-with. In addition, they feature 99.9% server uptime as well as 99.9% network uptime warranties.
Powered by:
HostCheetah Networks
Global Web Hosting, Domain Registration, and Internet Services
https://hostcheetah.net | http://hostcheetah.uk
PC Helper | Est 1996 - Web Hosting | US, AU, UK, Finland, Bulgaria | ![]()
https://pchelper.com