Overview
This article provides a broad overview of steps one can take to prevent the circumventing of OpenDNS services by users on your network.
Explanation
Savvy internet users may try to bypass OpenDNS services if your network security configuration allows them to change the local DNS IP server address to something other than the addresses of our public servers. This would render your security policies useless and may leave your network vulnerable. However, it is possible to not allow those other DNS services through your network firewall to the Internet, which will prevent these users from circumventing the protection.
General Instructions
Most routers and firewalls will allow you to force all DNS traffic over port 53, thus requiring everyone on the network to use the DNS settings defined on the router/firewall (in this case, OpenDNS). The preferred recommendation is to forward all DNS requests to go to the openDNS IP’s listed below. This way, you simply forward users’ DNS requests without them knowing, instead of having the possibility of someone manually configuring DNS and having it not work.
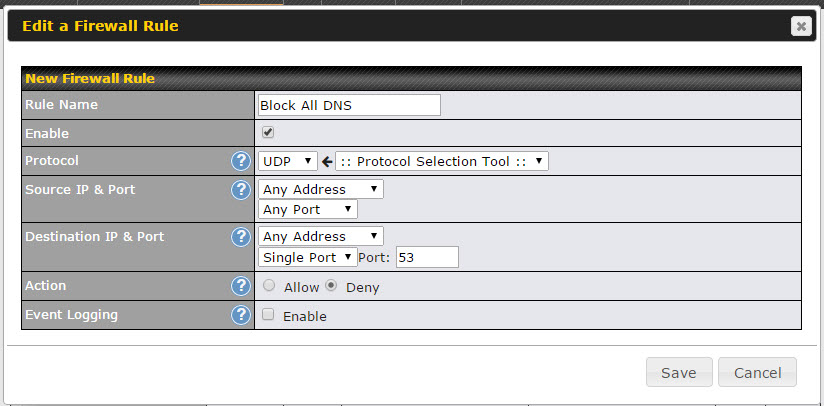
Essentially, you will want to create a firewall rule to only allow DNS (TCP/UDP) to OpenDNS’ servers and restrict all other DNS traffic to any other IPs. Ideally this filter or rule would be added to the firewall that is at the furthest edge of your network. In simple layman’s term, this would be defined similarly as below:
ALLOW TCP/UDP IN/OUT to 208.67.222.222 or 208.67.220.220 on Port 53
and
BLOCK TCP/UDP IN/OUT all IP addresses on Port 53
The first rule trumps the second rule. Put simply, any requests to OpenDNS will be allowed and any requests to any other IP will be blocked.
Depending on your firewall configuration interface, you may need to configure a separate rule for each of these protocols or one rule which covers them both.
The rule can be applied on either the firewall or the router, but normally is best placed on the device most at network edge. A similar rule could be applied to software firewalls installed on a workstation as well, such as the built-in firewall on Windows or Mac OS/X.
Unfortunately, individual configurations are not something OpenDNS is able to assist in supporting, as each firewall or router has a unique configuration interface and these vary greatly. If you are uncertain, you should check your router or firewall documentation or contact the manufacturer to see if this is possible with your device.